This blog post outlines the procedure to use the DPoD HSM on Demand service to carry out bring your own key for AWS.
Overview
The process comprises of the following operations
- Generate an external key in AWS
- Create a key
- Import token: ensures the import has to be done in a limited period of time before token expiration
- Wrapping key: key used to wrap the key to be transferred
- Convert the wrapping key certificate from DER format to PEM format
- Create a AES key, and wrap using AWS wrapping key
- Import wrapping key with the cmu tool
- Change wrapping key attribute to enable wrap+encrypt operations with the cmu tool
- Generate an AES key
- Wrap the newly created AES key with the wrapping key from AWS
- In AWS interface, import the wrapped key file and the token
Pre-requisites
An AWS with Key Management System must be activated
A HSM partition or a DPOD partition must be initialized and configured. FIPS mode may be enabled or disabled.
Step 1 – Generate an External Key in AWS
In Amazon KMS, go to Customer managed keys and create a key:
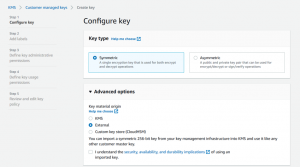
In step 1, select symmetric key and external in advanced options:
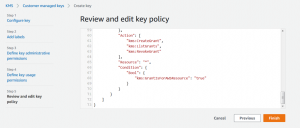
In steps 2,3 and 4 enter labels of your choosing and select key usage permissions, in particular, GrantIsForAWSResource:
Next select the RSAES_OAEP_SHA_256 Wrapping algorithm and download the wrapping key:
Save the wrapping key to your computer and then click next in the AWS dialog to show the following screen:
Leave this dialog open while we carry on with our next steps. We will return to this dialog in Step 3.
Step 2 – Import the wrapping key into the DPoD HSM-on-Demand Service
Start with extracting the ImportParameters.zip file that we downloaded in the previous step:
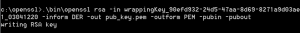
The uploaded wrapping key must be converted in PEM format to be uploaded onto the HSM partition. This can be accomplished using OpenSSL:
openssl rsa -in wrappingKey_90efd932-24d5-47aa-8d69-8271a9d03ae1_03041220 -inform DER -out pub_key.pem -outform PEM -pubin -pubout
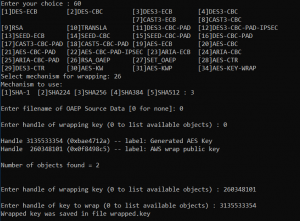
Next import the AWS wrap key onto an HSM partition and set the encrypt and wrapping attributes.
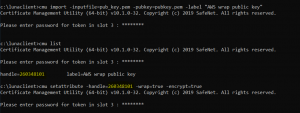
Use the cmu tool supplied with the DPoD client:
cmu import -inputfile=pub_key.pem -pubkey=pubkey.pem -label "AWS wrap public key" cmu list (get the handle ID) cmu setattribute -handle=260348101 -wrap=true -encrypt=true
Next we will create the key that we will be taking to AWS inside the DPoD Cloud HSM. To accomplish this we will use the ckdemo application that is provided by the DPoD client but any method of generating a HSM key is equally applicable.
- First launch ckdemo
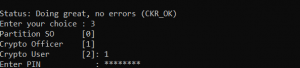
- Login to the DPoD partition – input 1,3,1
- Enter the PIN/password for your Crypto Officer
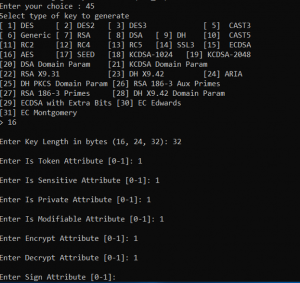
Now we can generate an AES key
- Choose option 45 (Generate Simple Key)
- Option 16 for AES
- Choose 32 byte key length for AES 256
- Enter 1 to activate all attributes
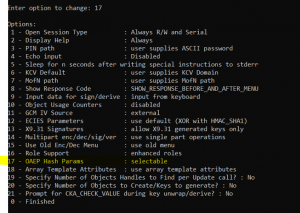
Next we will Wrap and export the key
- Continuing to use ckdemo, enter 98 for Options
- Now enter 17 – Configure OAEP hash params
- Then 0 – exit options
- Next select Option 60 – wrap key
- Then Option 26 – RSA OAEP
- Option 3 to use SHA 256
- 0 – no source data file
- Option 0 to list objects in the DPoD partition
- Enter the key handle for the wrapping key
- Enter the handle for the (AES) key we will be exporting to AWS
This will create a new file named wrapped.key
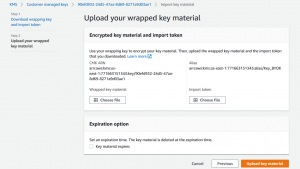
Step 3 – Upload the key to AWS
Now we return back to the AWS dialog we left at the end of step 1.
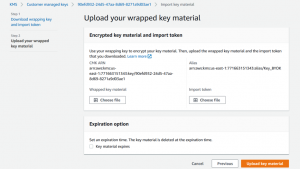
- First select “Choose File” for the Wrapped Key Material. Select the wrapped.key file that we created at the end of Step 2.
- Next select “Choose File” for the Import Token. Select the importToken_ file that we received in the ImportParameters.zip file during Step 1.
Press the “Upload key material” button to import our HSM sourced AES key and you should see the following success screen:

And that completes the process of BYOK from a DPoD Cloud HSM partition to AWS.